This blog post from the Nozomi Networks Labs team investigates attacks against a low-power radio frequency WAN technology that is widely used in industrial IoT networks.
Our research focused on the viability of discovering the transmission frequency of the IoT network, and jamming the signal to disrupt network communication. Although there are some practical limitations to the attack scenario we investigated, we clearly determined that there are potential attack vectors that should be considered as technology matures.
An Introduction to LoRaWAN Technology
LoRaWAN is a wireless technology that falls into the category of low-power wide-area networks (LPWAN). LoRaWAN is an open standard promoted by the LoRa Alliance, particularly for industrial IoT deployments. The technology usage includes devices that benefit from wireless communication and have requirements for long-distance communication and low power consumption.
This includes devices such as an intelligent water utility meter that would communicate water consumption amounts to the utility company, eliminating the need for an inspector to visit the residence every few months. Another usage could be the transmission of data from a gas pipeline that extends long distances across a variety of terrains that might lack proper infrastructure. In such a scenario, the cost of wireless communication technology would be a fraction of that required to interconnect all the equipment, for let’s say meteorological data. While this flexibility is related to the cost of available data rates, it is still an attractive solution for applications where a small amount of data is exactly what is needed.
While technology like this is being embraced across industries, we need to consider its possible impact on our lives. LoRa sensors (where LoRa is the modulation technology used in LoRaWAN), like many other wireless technologies, are susceptible to interference attacks that can make the LoRa signal unavailable to the recipient.
The interesting part is that such an attack would not be pragmatic, not only because of counter-measures from the modulation (such as frequency hopping) but also because of the long distances these sensors can be placed in. While experiments for jamming the LoRa signal have been conducted, we were more interested in exploring how you can actually deploy such an attack in the real world. We focused on understanding what the requirements of such an operation are, and investigating what an advanced persistent threat (APT) would do in such a scenario.
To understand these limitations, we investigated interrupting the signal first from a fixed frequency perspective and then from a frequency hopping perspective. The second term refers to the tactic used to protect the signal from interference by slightly changing the transmission frequency with a pseudo-random sequence known only to the legitimate transmitter and receiver.
We first considered the jammer. We wanted to implement something selective that would attempt to jam the attack during the time of the transmission. That made sense from a few perspectives. First, radio jammers are uncontrollably disruptive. That is an issue since we cannot do specialized targeting. We might disrupt our own infrastructure, or an unintended target. Also, they are easily detectable.
To achieve this, we considered two approaches. The first one was to time the transmission of LoRa packets. This approach could be considered because LoRa sensors send a few countable packets per day, usually in a predefined time range. The second approach was to initiate our attack when the sensor starts its transmission. The goal here was to send the jamming signal the moment the transmission starts from the sensors, to disrupt its payload. We decided to use the second approach as it has an advantage over the frequency hopping approach.
The issue we had with the second technique was that we needed to be close enough to the sensor to effectively jam the signal. There are several methods that can be utilized to locate a device from a radio signal. Any wave that propagates in a medium has a specific direction as it distances itself from its source. By using an array of antennas, you can derive the source location of that signal. It’s exactly what sonar does in submarines. Such an approach would need the proper synchronization of devices to calculate the time difference of arrival (TDoA) of the signal and the direction. Another attribute of a wave is its power. Under certain conditions you can estimate the distance to the sensor by measuring how strong or weak the signal is. The second approach is less accurate but it’s also less expensive to implement as you need just a single Gateway without any synchronization requirements.
Determining the Attack Scenario
For our experiment we decided to implement:
- A localization strategy based on the strength of the LoRa signal
- A jamming attack that activates when the sensor sends data
For the localization we used the Received Signal Strength Indicator (RSSI) value. This is a measurement of the power of the LoRa signal. The relation of RSSI and distance in LoRa can be given by the following formula:
RSSI= -10*n*log(10d)+A
Where d is the distance from the node and the measurement point, A is the received power when the distance between the two antennas is 1 meter, and n is the loss parameter or loss exponent which depends on environmental conditions. Solving for d we have the following equation:
d=10((A-RSSI)/10n)
Parameters A and n can be estimated with a margin of error that is heavily affected by the environment that the measurement is made in (building, urban area, rural area, etc).
Having our estimated distance from one place isn’t enough because we know the distance but not the direction. The sensor can be in any direction, creating a circle around the measurement point with diameter. We need at least three different points of measurements to be able to locate the sensor. This is the trilateration algorithm where the measurement of three points gives us the location of the LoRa sensor to the point where the circles intersect.
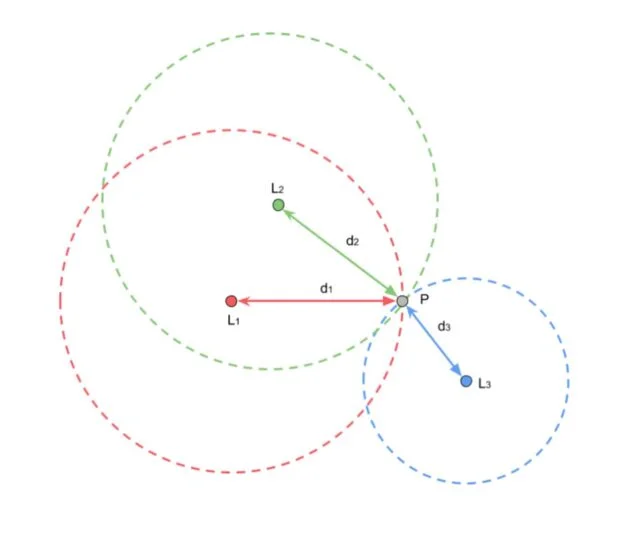
We can replicate the measurement as many times as needed. We can also add multiple points for more accuracy. If measurements are not extremely accurate, we can take the average of many measurements to provide an estimation.
To locate the signal we used an Arduino MKR WAN 1310 that can be programmed as an LoRa gateway. The Arduino is connected to a PCB and can be remotely controlled with a raspberry via a serial port. Connecting to the raspberry with 4G will allow us to move our detector in multiple remote locations.
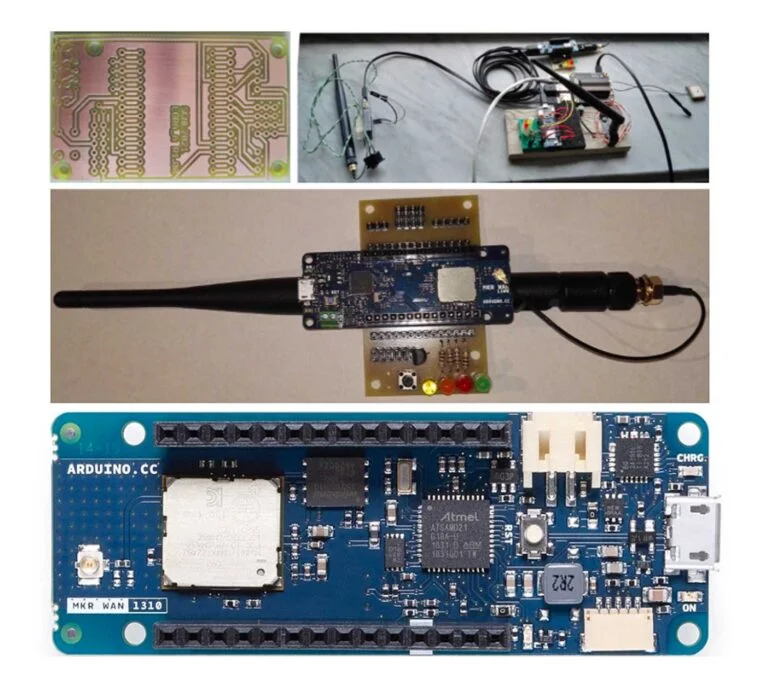
Identifying and Jamming the LoRaWAN Signal
For the purposes of the jammer, we used a Software Defined Radio (SRD) module. These devices are programmable signal processing devices that allow modulation and demodulation of a signal according to our needs.

The jammer attack consists of two phases:
- Detection of the LoRa signal. We used a series of band-pass filters to check all the available channels in the LoRa range. This enabled us to monitor multiple channels so that we were able to capture any possible packet transmission.
- Jamming of the LoRa signal. This involves sending a burst of energy to the frequency we need to jam. This results in the destruction of the LoRa signal. The legitimate gateway is forced to drop the packet, and valuable information is lost.
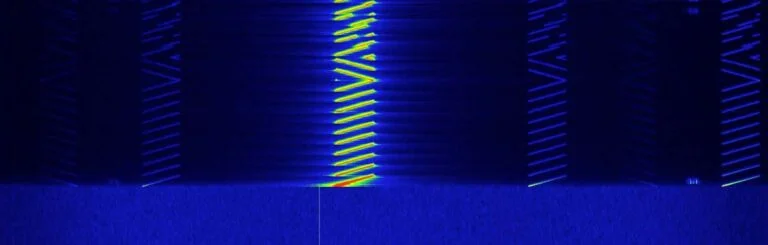
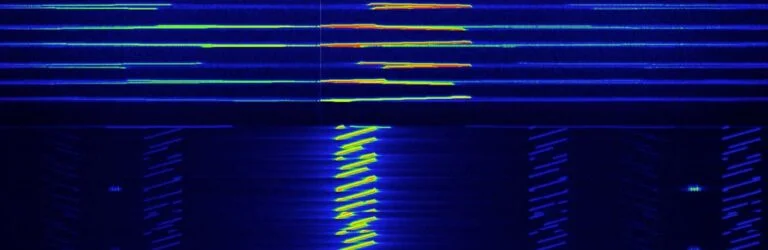
In our experiments we noticed that the packets were either dropped or the CRC of the packet was invalid. This meant that part of the packet was received from the gateway, but it was malformed so the gateway could not validate it and was forced to drop it.
To apply our approach in the real world, we decided to use drones. A drone can move across any terrain and gain adequate altitude to receive the signal. The RSSI can be quite accurate after a few measurements in the same location by averaging the values.
The approach here is to select a random location close to the facility, within a 5 to 10 km radius area. Within the receiving area of the LoRa signal, we can take multiple measurements to establish a good averaging RSSI value. We need to repeat the process in at least two arbitrarily selected locations, as long as they are not the same point. Using our trilateration algorithm, we can estimate the location of the sensor. The final stage is to approach the sensor and activate the selective jammer.

Conclusion
While the attack scenario we implemented has some limitations, such as a drone battery life of about 20 minutes, the research demonstrates that an attacker can completely ignore physical limitations to get closer to the target sensors as all the barriers can be bypassed by drones in order to automatically locate and disrupt part of the industrial communication infrastructure.
The key takeaway is that a pragmatic attack that considers the framework and properties of a system can be designed. As technology advances, we must be aware of these considerations to keep our system and infrastructure safe.








